Storage in Collaborative Networked Art Original
¶ 1 Leave a comment on paragraph 1 0 Transmission and Storage
¶ 2 Leave a comment on paragraph 2 0 Alexander Graham Bell’s first telephone voice transmission (March 10, 1876): “Mr. Watson, come here. I want to see you.”
¶ 3 Leave a comment on paragraph 3 0 If Bell had placed that call today: “You’ve reached Thomas Watson. I’m not available to take your call right now, but if you leave a message at the sound of the tone, I’ll get back to you as soon as I can. Thanks.”
¶ 4 Leave a comment on paragraph 4 0 One purpose of the telephone network is aural telepresence: the network collapses our sense of space by transmitting data in nearly real time. AT&T encapsulated this idea in their early 1980s advertising slogan: “Reach out and touch someone” (Porticus Centre, 2004).
¶ 5 Leave a comment on paragraph 5 0 But even in the 1980s, this metaphor missed some of the important ways in which people used the telephone network. As a child, I called the local time and weather number more than any other (Telephone World, 2003), since when the temperature dropped low enough, the dress code at my school was relaxed and we could wear warmer clothes. When people called our home phone, they were often greeted by our answering machine, which used one cassette tape to play our greeting and a second to record incoming messages.
¶ 6 Leave a comment on paragraph 6 0 Today, we increasingly use our phones — whether mobile phones or old-fashioned home phones — to connect with voicemail systems, to check the status of banking transactions and airline flights, or to buy movie tickets. We routinely receive automated calls reminding us to do everything from pay overdue bills to vote for political candidates. Instead of speaking live to another person, we record a message on a server’s hard drive or perform queries on a database or hopelessly scream commands to a computer-driven menu system. In these cases, we are not reaching out and touching someone. We are reaching out and touching storage.
¶ 7 Leave a comment on paragraph 7 0 Just like person-to-person phone calls, these additional applications for the telephone network still require nearly real-time transmission. Equally important, though, they require a storage mechanism accessible on the network: the cassette tape on the answering machine, the hard drives on the corporate phone system, or the bank database accessed via a VoiceXML-style bridge protocol (VoiceXML Forum, 2009). Without some kind of storage, the movie tickets would never be purchased, the weather never reported, and the voice message never retrieved.
¶ 8 Leave a comment on paragraph 8 0 Storage on the Internet
¶ 9 Leave a comment on paragraph 9 0 With the telephone network, storage is an important extension that enables new classes of applications. Computer networks, on the other hand, have included storage as an integral component since their early development. The first version of the FTP protocol, a common standard for transmitting files across computer networks, was published in 1971 (Bhushan, 1971), predating even the TCP/IP protocol. Relational Software (now Oracle) released the first SQL database in 1979 (Oracle, 2009). Tim Berners-Lee initially proposed the World Wide Web in 1989, touting it as a distributed, linked system for storing information, notes, and documents and connecting multiple existing databases. Without storage mechanisms, many of the networked applications we take for granted (even e-mail) would be difficult to realize (Berners-Lee, 1989).
¶ 10 Leave a comment on paragraph 10 0 The rise of Web 2.0 applications, cloud computing, and browser-based technologies such as AJAX have further emphasized the role of networked storage in Internet applications. In a 2005 article about Web 2.0, Tim O’Reilly noted the importance of databases on the Internet: “Every significant Internet application to date has been backed by a specialized database… As Hal Varian remarked in a personal conversation last year, ‘SQL is the new HTML.’” (O’Reilly, 2005:3).
¶ 11 Leave a comment on paragraph 11 0 Because computer networks are implemented through a combination of hardware and software, network applications are able to take advantage of a staggering variety of storage mechanisms, protocols, and structures, ranging from simple file storage (e.g. static web pages) to structured databases which can potentially be queried, manipulated, updated, and expanded by any person or device connected to the network.
¶ 12 Leave a comment on paragraph 12 0 Database Aesthetics and Collaboration
¶ 13 Leave a comment on paragraph 13 0 In the media arts, the role of storage has figured prominently in recent discourse and practice. Christiane Paul notes the prevalence of the term “database aesthetics” which she defines as “the aesthetic principles applied in imposing the logic of the database to any type of information, filtering data collections, and visualizing data.” (Paul, 2007: 95). Paul cites The Secret Lives of Numbers (Levin, 2002), an interactive visualization of the popularity of numbers on the Internet, as one prominent example of database aesthetics in practice (Paul, 2007: 106).
¶ 14 Leave a comment on paragraph 14 0 Lev Manovich also writes about the “dominance of database form in new media.” He notes that its dominance reflects broader cultural perspectives: “… if … the world appears to us as an endless and unstructured collection of images, texts, and other data records, it is only appropriate that we will be moved to model it as a database” (Manovich, 2000:177). Manovich also argues that the focus on database form in turn influences culture: “As a cultural form, database represents the world as a list of items and it refuses to order this list”, competing against narrative forms and their “cause-and-effect trajectory” as the means by which to “make meaning out of the world” (Manovich, 2000:181).
¶ 15 Leave a comment on paragraph 15 0 This chapter focuses not on this broad role of storage in media art, but rather on the specific role of storage in collaborative creativity within networked music. I explore how networked participants, whether they are a group of trained musicians, casual users, or a combination of the two, employ storage as a medium for communication and as a mechanism for collaboration. I also hope to reveal how the conception and realization of networked art works relative to the design and implementation of storage mechanisms affects the nature of collaborative creativity within them.
¶ 16 Leave a comment on paragraph 16 0 For the purposes of this chapter, I define a division between transmission-focused works and storage-focused works. The former facilitate real-time communication among network nodes or participants. Any storage functionality that exists is either short-term (e.g. buffering audio or video feeds to reduce dropouts) or peripheral (e.g. an archival recording used solely to document the work). Examples include multi-location performances such as The Technophobe and the Madman (Didkovsky et al, 2001), telepresence environments such as Global String (Tanaka and Toeplitz, 1998), and web-based collaborative improvisations such as Public Sound Objects (Barbosa, 2008), a class of projects which Barbosa has dubbed “shared sonic environments” (Barbosa, 2003:57).
¶ 17 Leave a comment on paragraph 17 0 In contrast, storage-focused works would be difficult or impossible to realize without a networked storage mechanism. Storage-focused works also typically transmit information across networks; it is the integration of a storage component that distinguishes them. Examples include social spaces such as ItSpace (Traub, 2007) and collaborative creation tools such as FMOL (Jordá, 2000). If transmission-focused works collapse geographic space, then storage-focused works collapse time: networked participation need not be simultaneous.
¶ 18 Leave a comment on paragraph 18 0 This division between transmission-focused and storage-focused works oversimplifies the diverse field of collaborative, networked art and ignores a fertile area of ambiguity between these categories, but it buy Premarin online is nonetheless a useful lens through which to consider networked art practices. In the following sections, I present a series of paired analyses of works that differentially emphasize transmission and storage or that employ different approaches to storage. Each analysis focuses on different opportunities, challenges, and issues related to storage in networked art:
¶ 19 Leave a comment on paragraph 19 0 – Maintaining the Web Under Less Than Obvious Circumstances (Rova Saxophone Quartet, 1989) and In Sand: Human Computation (Collins, 2007), frame a discussion of composition and improvisation.
¶ 20 Leave a comment on paragraph 20 0 – Borrowing and Stealing (Stone, 1989) and Wheelies (Brown, 1992), both written for the network computer band, The Hub, initiate a discussion on the influence of technology on network design and on collaborative models of shared material and shared control.
¶ 21 Leave a comment on paragraph 21 0 – Active storage systems, which autonomously modify their contents over time, are explored through Max Neuhaus’ participatory radio works Public Supply I (Neuhaus, 1966) and Radio Net (Neuhaus, 1977).
¶ 22 Leave a comment on paragraph 22 0 – WebDrum (Burk, 2000a) and the commercial web service Jamglue (2006) raise issues about network latency and the persistency of storage.
¶ 23 Leave a comment on paragraph 23 0 – Bicycle Built for 2,000 (Koblin and Massey, 2009) and my own Graph Theory (Freeman, 2006) explore the level of awareness of storage mechanisms by participants.
¶ 24 Leave a comment on paragraph 24 0 I hope that the insights derived from these analyses about roles of storage in networked art, approaches to using storage in networked art, and challenges and opportunities associated with incorporating storage into networked art, will help to bring new perspectives to our study of existing works and to our creation of new works.
¶ 25 Leave a comment on paragraph 25 0 In this chapter, I try not to make value judgments about the works I discuss. I never imply that storage-focused works are somehow “better” in any qualitative or quantitative manner than transmission-focused works — only that they create particular opportunities and challenges to consider with respect to collaborative creativity.
¶ 26 Leave a comment on paragraph 26 0 All of the examples in this chapter are from networked music, since that is the field with which I am most familiar. Given the networked format of this book, I encourage you to expand the scope of this discussion by contributing your own examples and thoughts to this chapter.
¶ 27 Leave a comment on paragraph 27 0 Composition and Improvisation
¶ 28 Leave a comment on paragraph 28 0 Networks Without Technology
¶ 29 Leave a comment on paragraph 29 0 Collaborative networked art need not involve computers or telephone systems or electricity of any kind. In a sense, almost any performance is networked: performers transmit visual and aural stimuli to each other that influence the performance.
¶ 30 Leave a comment on paragraph 30 0 Using a topology scheme such as that proposed by Weinberg (2005: 33-37), we could try to describe the nature of such networks more precisely: the relationship between orchestral players and a conductor might be classified as a centralized, one-way, synchronous flower topology, while the interconnections among members of a small jazz combo might be classified as a decentralized, interdependent, synchronous star topology. Musical scores might act as data stores, though they are not typically accessible over the network: one musician cannot usually see another’s part.
¶ 31 Leave a comment on paragraph 31 0 When artists consciously consider the topology and the transmission and storage mechanisms of a network, that network can become integral to the conception and realization of the work — even if that network does not involve any technology. This section considers two such works by the Rova Saxophone Quartet and Click Nilson / Nick Collins.
¶ 32 Leave a comment on paragraph 32 0 Rova
¶ 33 Leave a comment on paragraph 33 0 The Rova Saxophone Quartet, a preeminent improvising jazz ensemble, created a unique physical network for Maintaining The Web Under Less Than Obvious Circumstances (Rova Saxophone Quartet, 1989). In his liner notes for the CD, Derek Richardson explains: “There are four red flags and seven fans as well as hats, balls and various other hand signals that are related to everything from speed and volume to the playing of harmonicas. Any of the four musicians can give a cue at any time and dramatically alter the course of the piece.” Richardson notes that cues may indicate anything from asking other players to join in duos or trios or to imitate each other to indicating note cutoffs (Richardson, 1997).
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 35 Leave a comment on paragraph 35 0
¶ 36 Leave a comment on paragraph 36 0 Media Example 1: Rova Saxophone Quartet, “Less Than Obvious” (Rova Saxophone Quartet, 1989). Rastascan BRD 027, 1997.
¶ 37 Leave a comment on paragraph 37 0 In their own publicity materials, Rova describes their focus as “explor[ing] the synthesis of composition and collective improvisation” (Rova Saxophone Quartet, 2009). Their network design for Maintaining the Web, which evolved out of collaborations with the Margaret Jenkins Dance Company and with John Zorn, facilitates exactly this synthesis of composition and improvisation.
¶ 38 Leave a comment on paragraph 38 0 In this work, Rova’s composition is the predetermined set of objects and hand signals, along with the formal protocol that defines the meaning of particular objects and gestures. Composition is an act of network protocol design, and that protocol then supplements other channels of visual and aural communication. The network is what gives the work its identity as a composition: something that is recognizable as the work even though it may be played differently each time (see Richardson, 1997 for further details).
¶ 39 Leave a comment on paragraph 39 0 In performance (Media Example 1), Rova improvises, using the network to communicate with and influence each other; they do not play from a score. In the moment of the performance, the composition does not exist in a vacuum; the players must use the aural network (their ears) and their innate musicality to shape each unique performance. The album itself demonstrates the role of improvisation in shaping the work: Rova member Larry Ochs confirms in an interview that the six diverse tracks on the disc are simply six different “takes” of the composition (Montgomery, 1997).
¶ 40 Leave a comment on paragraph 40 0 Nilson/Collins
¶ 41 Leave a comment on paragraph 41 0 Like Rova’s Maintaining the Web, British musician Nick Collins (who often performs under the name Click Nilson) has developed formalized networks for communication among musicians during a performance. In contrast to Rova’s network, information is exchanged via written instruction lists. Each instruction list becomes a storage mechanism on the network that can be preserved, modified, copied, and transmitted during the performance.
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 43 Leave a comment on paragraph 43 0
¶ 44 Leave a comment on paragraph 44 0 Media Example 2: Excerpt from Click Nilson’s “In Sand: Human Computation” (Collins, 2007). Richard Padley, electric guitar; Satoko Fukuda, violin; Danny Kingshill, cello; Gus Garside, double bass; Thor Magnusson, laptop. Toplap 001: A Prehistory of Live Coding, 2007.
¶ 45 Leave a comment on paragraph 45 0 Collins (2009) describes how one such piece, In Sand: Human Computation (Collins, 2007 and Media Example 2), was performed: “[The] musicians, when not playing, had an active role in drawing out new instructions and modifying existing ones. I had a facilitation role, and wandered through the room helping to update papers and exchange them [between musicians].” A more formal version of this network is described in his sample score, An Instructional Game for 1 to many musicians (Collins, 2005), though Collins acknowledges that this score, which was written as a fictional historical precedent for his work, has never been performed as written (Collins, 2009).
¶ 46 Leave a comment on paragraph 46 0 Like Rova, Collins combines elements of composition and improvisation in these works using game-like elements. But the use of storage on the network — the written instruction lists — brings notable differences to both the interaction of the musicians over the network and to the role of composition.
¶ 47 Leave a comment on paragraph 47 0 Because they communicate via written instruction lists rather than visual cues, musicians in Collins’ work interact differently over the network than the members of Rova. Rova’s musicians transmit visual cues to each other that are perceived in nearly real time and have an immediate effect on the cue’s recipient(s). Communication is largely event driven; a cue may trigger a change in volume, a note cutoff, or a new imitative texture.
¶ 48 Leave a comment on paragraph 48 0 Collins’ musicians exchange written instruction lists with each other that contain directions to be followed over an extended period of time. Once received, instruction lists are not usually executed immediately; at the very least, musicians must take some time to read and understand the new instructions in front of them. And those lists remain in effect for extended periods of time; as the performance continues to iterate, the lists serve as the basis for future modifications and exchanges.
¶ 49 Leave a comment on paragraph 49 0 Collins’ use of storage also transforms the role of composition. Like Rova, portions of the work are composed in advance; Collins created a brief textual explanation of the work as well as an initial list of instructions. But while Rova’s musicians draw from a pre-determined collection of cues during their performance, Collins’ musicians (and Collins himself) actually change, add, delete, and copy instructions on their lists. Composition becomes part of the performance, not only something that precedes it. The networked storage mechanism enables the musicians to continually recompose the score.
¶ 50 Leave a comment on paragraph 50 0 This particular synthesis of composition and improvisation, a kind of performative composition, has gained traction in recent years through the live coding movement (Toplap, 2008), in which performers write algorithmic code on stage, project their laptop screens for the audience to see, and execute that code as they write it to generate music and/or visuals. Collins himself is a leading practitioner in the field.
¶ 51 Leave a comment on paragraph 51 0 Influence of Technology on Network Design
¶ 52 Leave a comment on paragraph 52 0 When artists design networks, practical issues inevitably influence the design process. The flags and signals used by saxophonists in Rova were large, colorful, and easy for players to spot from the opposite end of the performance space. Collins had to help musicians exchange instruction sheets during his performance so that they could focus more on playing music than on network mechanics.
¶ 53 Leave a comment on paragraph 53 0 When technology factors into these networks, practical considerations can become even more important. The strengths and limitations of different software programs, hardware systems, and communications protocols influence the ease with which different network designs can be realized. The Hub, which dubs itself as “the original computer network band” and began playing together thirty years ago (The Hub, 2009), exemplifies the influence of technology on network design.
¶ 54 Leave a comment on paragraph 54 0 Each member of The Hub performs on his own computer with his own software, but those computers are connected during performance to share data storage and/or messages based on the particular rules and protocols defined for each composition. Like Rova and Collins, The Hub’s performances incorporate elements of composition — defining the rules and protocols and writing the computer software — as well as improvisation — performing live with that software over the network.
¶ 55 Leave a comment on paragraph 55 0 Initially, members of The Hub networked their computers via a serial link to a central computer (also called “The Hub”) that served as a shared memory for the ensemble (Brown and Bischoff, 2002: 2.1). Musicians did not send messages directly to each other; instead, they wrote data to the shared memory so that other musicians could later retrieve it. Scot Gresham-Lancaster, a member of The Hub, described that network as “a conceptual place in which we shared the active components of any given piece” (Gresham-Lancaster, 1998: 41).
¶ 56 Leave a comment on paragraph 56 0 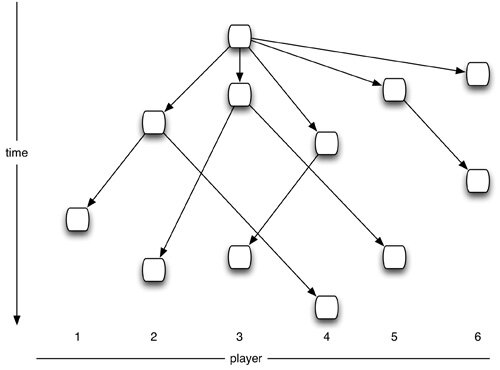
Figure 1: As material is shared and modified in the networked storage in “Borrowing and Stealing” (Stone, 1989), it creates a tree structure of derivative variations.
¶ 57 Leave a comment on paragraph 57 0 Borrowing and Stealing (Stone, 1989), written for this early incarnation of The Hub’s network, exemplifies the influence of the network’s capabilities on the music’s design. In Stone’s piece, each of the musicians writes melodic data to their own portion of the shared memory. Players then read another musician’s melody from the shared memory. They transform that melody, play it back, and finally place the new version in their section of the memory. Since The Hub usually began this piece with a single melody from a single player, the structure of the performance resembles a tree (Figure 1): the root node is the initial melody, which then branches out to child nodes as different players grab the melody and transform it. As those children are in turn transformed, new generations of nodes on the tree are created.
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 59 Leave a comment on paragraph 59 0
¶ 60 Leave a comment on paragraph 60 0 Media Example 3: Excerpt from “Borrowing and Stealing” (Stone, 1989). Available on The Hub: Boundary Layer, Tzadik 8050-3, 2008.
¶ 61 Leave a comment on paragraph 61 0 In performance (Media Example 3), the music sounds, as Hub member Chris Brown notes, like “a kind of metamorphosing minimalism” (Brown and Bischoff, 2002: 3.1). Melodic motives loop repeatedly, layer upon themselves in various variations, and gradually turn into seemingly new musical material as they are iteratively modified. Because the only way to communicate across the network is to share music — not instructions or events — and because the only way to create music is to draw from the material on the network, the music exhibits a notable economy of means.
¶ 62 Leave a comment on paragraph 62 0 From Shared Material to Shared Control
¶ 63 Leave a comment on paragraph 63 0 In 1990, The Hub updated the technical architecture of their network, leaving behind the custom-built, slow, antiquated, and unreliable RS-232-based system. In its place, they adopted an off-the-shelf network built with MIDI (Musical Instrument Digital Interface), a standard originally developed for communication among electronic musical instruments that is now used in everything from polyphonic cell phone ringtones to theatrical lighting equipment to music software. At the heart of their network was a MIDI patchbay interface that enabled any member of the ensemble to send messages individually to any other member.
¶ 64 Leave a comment on paragraph 64 0 Their move to off-the-shelf hardware and an industry-standard network protocol undoubtedly made their system more robust and their software easier to develop. The network’s new functionality also spurred the ensemble to think about network design in new ways. As Gresham-Lancaster notes: “This new context created new ways of thinking about the concept of a network for making music” (Gresham-Lancaster, 1998:42). But in adopting this MIDI-based system, the group also gave up their central, shared repository of data that players could manipulate and from which they could draw.
¶ 65 Leave a comment on paragraph 65 0 Wheelies (Brown, 1992), written for the MIDI-based Hub, demonstrates how the group’s thinking about the network evolved as their technology changed. In the work, players communicate not by sharing musical material with each other, but by sharing control of their computers with each other. Network interaction moves to an event-driven model in which musicians send instructions that change parameters or trigger actions.
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 67 Leave a comment on paragraph 67 0
¶ 68 Leave a comment on paragraph 68 0 Media Example 4: Excerpt from “Wheelies” (Brown, 1992). Available on The Hub: Boundary Layer, Tzadik 8050-3, 2008.
¶ 69 Leave a comment on paragraph 69 0 In Wheelies, each player controls his own timbre and pitch material, but other members of the ensemble determine his rhythms. Global clock messages send the tempo from the “conductor” (one of the musician’s computers) to all other players to maintain synchronization. Each player can then control rhythmic parameters (e.g. note subdivisions, note density, and meter) by sending messages to other individual players. Finally, each player can send global messages that mute and unmute all sound or force everyone’s rhythm parameters to update simultaneously (Brown and Bischoff, 2002:4.3).
¶ 70 Leave a comment on paragraph 70 0 The Hub’s change in network technology prompted a shift from a storage focus to a transmission focus and from a data-driven, shared material model to an event-driven, shared control model. The musical texture of Wheelies (Media Example 4) is correspondingly different. Instead of a slowly-evolving collection of polyphonic voices, it is a tightly synchronized series of episodic gestures that alternate between periods of stasis and sudden moments of change as players update each others’ parameters and send global commands.
¶ 71 Leave a comment on paragraph 71 0 Active Storage
¶ 72 Leave a comment on paragraph 72 0 Types of Storage
¶ 73 Leave a comment on paragraph 73 0 The presence or absence of storage on The Hub’s network influenced the music they composed and performed together. But network design considerations go beyond the mere presence or absence of storage. Different kinds of networked storage mechanisms facilitate different kinds of artistic applications. A flat-file architecture encourages the archiving and retrieval of discrete activities. A relational database or shared memory unit encourages the structured, collaborative manipulation and retrieval of data.
¶ 74 Leave a comment on paragraph 74 0 Some networked storage devices not only respond to messages to store, retrieve, and transform their data; they also actively and autonomously transform that data themselves. For instance, they may degrade or discard data over time, limiting the span of their memory, or they may iteratively mix or merge data elements. Two early networked sound works by Max Neuhaus demonstrate the influence of such unique storage systems on a work’s network design and musical content: Public Supply I(1966) and Radio Net (1977).
¶ 75 Leave a comment on paragraph 75 0 Neuhaus
¶ 76 Leave a comment on paragraph 76 0 In both works, Neuhaus’ core idea was to “combine the public telephone network and radio broadcast [to] make a virtual aural space in which a large number of people can be at the same time” (Neuhaus, 1994). Participants called a radio station during the live event and Neuhaus combined the sounds from multiple callers, broadcasting the result live on the radio station.
¶ 77 Leave a comment on paragraph 77 0 In Public Supply I (Neuhaus, 1966), performed at WBAI radio in New York, there was no storage mechanism; sounds were manually mixed and broadcast over the radio as they came in over ten telephone lines. The radio broadcast (Media Example 5) has an episodic feel to it as callers phone in, create their own distinctive layer in the mix, and then eventually disconnect. Each caller’s aural contribution is distinctive. Not only is the timbre of each voice unique, but so is the content: some speak, some scream, some sing, and many produce sound by other means — trumpets, harmonicas, stereos, and so on.
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 79 Leave a comment on paragraph 79 0
¶ 80 Leave a comment on paragraph 80 0 Media Example 5: Excerpt from “Public Supply I” (Neuhaus, 1966). Complete recording is available on Neuhaus’ web site.
¶ 81 Leave a comment on paragraph 81 0 Radio Net (Neuhaus, 1977) explores Neuhaus’ core idea on a larger scale: the two-hour national broadcast event brought together ten thousand callers. Equally important, Neuhaus altered both the format of the sonic contributions and the manner in which they were processed. Instead of open-ended participation, callers were specifically asked to whistle, creating a more cohesive but less diverse timbral sound world. Neuhaus also implemented an automated mixing system; custom circuitry analyzed the pitch of each whistle to set its prominence in the mix.
Audio clip: Adobe Flash Player (version 9 or above) is required to play this audio clip. Download the latest version here. You also need to have JavaScript enabled in your browser.
¶ 83 Leave a comment on paragraph 83 0
¶ 84 Leave a comment on paragraph 84 0 Media Example 6: Excerpt from “Radio Net” (Neuhaus, 1977). Complete recording is available on Neuhaus’ web site.
¶ 85 Leave a comment on paragraph 85 0 Active Storage in Radio Net
¶ 86 Leave a comment on paragraph 86 0 Radio Net also added an active, short-term networked storage mechanism. Taking advantage of the physical structure of the National Public Radio network on which the work was broadcast, Neuhaus created loops over the wires connecting studios in different cities to the main control center in Washington, DC. Sounds were circulated over those loops again and again; with each successive iteration, frequency was shifted and gain was reduced.
¶ 87 Leave a comment on paragraph 87 0 This storage system functioned in much the same way as an analog tape loop or a digital delay but was implemented through the network itself. The network did not contain a storage mechanism: it was a storage mechanism. The network continuously retransmitted signals, mixing recent sounds with older ones, to build up complex textures over time. Because the gain of the signal was reduced with each iteration through the loop, the storage was short term: sounds slowly faded into the background and eventually disappeared from the texture altogether.
¶ 88 Leave a comment on paragraph 88 0 The broadcast of Radio Net (Media Example 6) sounds dramatically different than Public Supply I. Much of this stems from the limitation of sonic contributions to whistling; individual callers lose their distinct identities within the texture. But the unique qualities of the active storage mechanism give rise to equally significant changes in the structure of the sounds. Just as whistles are the unifying sound, the glissando is the unifying gesture. Melodic motives and steady tones do emerge, but inevitably the texture returns to a glissando as the material is sent through the loop and its frequency is shifted. (Glissandi are also a common gesture in the original whistling sounds from callers, creating a strong connection between sound sources and storage processing.) The glissandi vary in their nature, but they remain the dominant gestural force throughout the work.
¶ 89 Leave a comment on paragraph 89 0 Latency and Persistency
¶ 90 Leave a comment on paragraph 90 0 Storage to Circumvent Latency
¶ 91 Leave a comment on paragraph 91 0 Network communication rarely takes place instantly. In a local, physical performance environment, the speed of sound and light cause negligible delays. On the Internet, such delays, augmented by the practical limitations of network traffic routing, can lead to noticeable latency. And if continuous media streams are buffered to reduce the risk of dropouts from lost packets, latency can increase substantially.
¶ 92 Leave a comment on paragraph 92 0 A Stanford University study has shown that for musicians, latency as low as 20 milliseconds can still transform the experience of performing at a distance; as rhythmic cues arrive late, the performance tempo gradually slows down (Chafe et al, 2004). Musicians have developed a variety of strategies to cope, including the adoption of musical styles that eschew tempo synchronization, as in sections of The Technophobe and the Madman (Didkovsky et al, 2001), and artificial increases to latency to maintain beat, but not measure, synchronization, as in NinJam (CockosIncorporated, 2005).
¶ 93 Leave a comment on paragraph 93 0 Artists have also used storage mechanisms to circumvent the effects of latency in their network designs. For instance, participants may contribute data rather than events, collaboratively but asynchronously manipulating a shared data structure. Such strategies are similar to those employed by The Hub’s original network (as in Borrowing and Stealing), though that network usually operated over a local area. Collaborative text editors such as SubEthaEdit (CodingMonkeys, 2009) and Google Docs (Google, 2009) are corresponding examples of wide-area collaboration using shared storage in the domain of text editing.
¶ 94 Leave a comment on paragraph 94 0 With these types of networks, the design questions move from latency to persistency. Must participation still be simultaneous, or should each user individually manipulate the data store over the course of hours, weeks, or months? Is the data store a permanent entity that can be archived, retrieved, and shared, or does it exist only during a single performance event? Do participants focus more on the creation of a finished product or on the process of collaborative creation?
¶ 95 Leave a comment on paragraph 95 0 Storage and Simultaneous Participation
¶ 96 Leave a comment on paragraph 96 0 WebDrum (Burk, 2000a) focuses on simultaneous participation and on the experience of collaboration. Users log in to the web-based drum machine, enter a “jam room,” and begin creating beats with other users (Media Example 7). Each user grabs control of individual layers of the drum machine, modifies the rhythmic motives and instruments for those layers, and controls global parameters such as tempo, key, and tuning. A text-based chat helps users plan their collaborative actions.
¶ 97 Leave a comment on paragraph 97 0 [flashvideo file=http://freeman.networkedbook.org/media/freeman/media-example-7.flv image=http://freeman.networkedbook.org/media/freeman/media-example-7.jpg width=500 height=432 /]
¶ 98 Leave a comment on paragraph 98 0 Media Example 7: Video capture of a jam session on WebDrum (Burk, 2000).
¶ 99 Leave a comment on paragraph 99 0 WebDrum makes no distinction between creation and performance or between process and product. The multi-track arrangement of patterns loops continuously as the material is edited. When the last player leaves the jam room, the data is deleted from the server and cannot be accessed again.
¶ 100 Leave a comment on paragraph 100 0 When I have demonstrated WebDrum to my students by holding group jams, the environment has proven to be fun and engaging. As more people join a jam room, complex textures emerge and musical material evolves rapidly. As users take control of tracks or global parameters from each other, they exchange roles within the collaboration, focusing on different layers of material.
¶ 101 Leave a comment on paragraph 101 0 Yet WebDrum suffers from a fundamental problem, as Burk notes: “The WebDrum is not yet a popular website. So, when people log in they often have no one to play with” (Burk, 2000b). Since WebDrum preceded the growth of online social networks, it has stood in isolation on the Web, and this has surely impeded its adoption. Yet even today, dependency on a critical mass of simultaneous online participants can be problematic.
¶ 102 Leave a comment on paragraph 102 0 Persistent Storage
¶ 103 Leave a comment on paragraph 103 0 In contrast, Jamglue (2009) focuses on networked collaboration through a storage space shared over an extended period of time. Users of this commercial web service launch a Flash-based multi-track audio editor (Figure 2), modeled after programs like GarageBand (Apple Computer, 2009), to create and remix music. Once they are happy with their music, they post it publicly on the site, where other users can listen, vote, and comment on it.
¶ 104 Leave a comment on paragraph 104 0 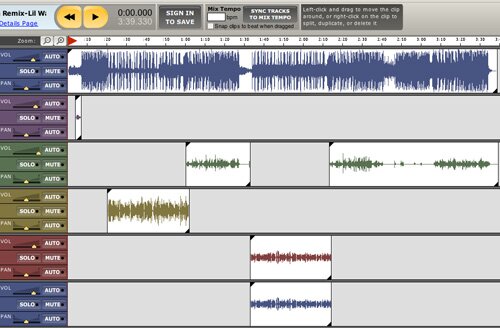
Figure 2: Screen shot of the main Jamglue user interface.
¶ 105 Leave a comment on paragraph 105 0 Because the authoring environment exists solely on the web, Jamglue users share much more than their finished products. Other Jamglue users can access their multi-track sessions in the Flash editor and create and post their own derivative remixes, creating a tree of connections similar to that of Phil Stone’s Borrowing and Stealing (Figure 1). They can also use the individual sounds from any song on the site in their own work.
¶ 106 Leave a comment on paragraph 106 0 Unlike WebDrum, Jamglue focuses on the products (the posted mixes) far more than the process, and the networked collaboration among users does not take place in real time; users are not even aware of who is using the site at the same time. A comparison of WebDrum to Jamglue would be unfair; Jamglue is a well-funded startup company while WebDrum was the quick creation of a music technologist, and each application has dramatically different goals. Yet Jamglue has undoubtedly been a success. According to the company, it currently boasts over 2 million posted mixes by over 1 million registered users (Jamglue, 2009).
¶ 107 Leave a comment on paragraph 107 0 Read and Write
¶ 108 Leave a comment on paragraph 108 0 Storage in the Background
¶ 109 Leave a comment on paragraph 109 0 With sites such as Jamglue, interaction with networked storage is core to the user experience: participants consciously store their own mixes on the site and retrieve mixes and sounds stored by others. But on the Internet, interaction with networked storage often takes place in the background; sometimes, we are not even aware it is happening. For example, when we visit a web site, a server log stores statistics about the content we view; this data is later analyzed to track usage patterns. And when we browse and purchase products, our shopping decisions are stored to provide future purchase recommendations.
¶ 110 Leave a comment on paragraph 110 0 There are many reasons such storage tasks might take place in the background and pattern baldness treatment without user intervention: their frequency might otherwise prove disruptive to the interface, or designers may (for better or worse) want to discourage objections to such data collection by reducing awareness of its existence. For artists, a new set of questions arises in network storage design. What level of awareness of networked storage is desirable for a work? How does that awareness affect the experience of the work?
¶ 111 Leave a comment on paragraph 111 0 Different Participants, Different Levels of Awareness
¶ 112 Leave a comment on paragraph 112 0 In my own project, Graph Theory (Freeman, 2006), I de-emphasize networked storage in the main interface design to encourage participants to focus on their individual experience with the work. On the web site, users navigate among sixty-one short musical fragments for solo violin to create their own unique path through the piece (Media Example 8). Each navigation decision they make is anonymously logged to a database, but the only reminder of this networked component in the interface is a subtle series of color changes to indicate the relative popularity of different navigation options. The interface encourages users to explore the fragments to create their own unique encounter with the piece; the design discourages them from considering the implications of their actions on the networked storage.
¶ 113 Leave a comment on paragraph 113 0 In this manner, the individual user experience with Graph Theory corresponds to Manovich’s notion of interactive narrative or “hyper-narrative,” in which the user “is traversing a database, following links between its records as established by the database’s creator.” Manovich argues that such hyper-narratives do not usually meet the criteria of a proper narrative (Manovich, 2000: 182). Graph Theory’s abstract musical content cannot easily be understood in the context of those narrative forms, but a similar tension does exist in the domain of musical form.
¶ 114 Leave a comment on paragraph 114 0 Music theorist Jonathan Kramer writes about Stockhausen’s idea of moment form, a collection of self-contained musical building blocks: “Since moment forms verticalize time, render every moment a Now, avoid functional implications between moments, and avoid climaxes, they are not beginning-middle-end forms. Although the piece must start for simple practical reasons, it may not begin; it must stop, but it may not end … the order of moments must appear to be arbitrary for the work to conform to the spirit of moment form” (Kramer, 1978:180-181). Graph Theory’s individual musical fragments bear a strong resemblance to moments, and the multiplicity of possible arrangements of those fragments recalls moment form. Yet Graph Theory breaks from moment form in its insistence that the order of its fragments does matter: it is the primary creative activity of web site users. And while no single order is preferable, some are more effective than others, and each brings a different experience to hearing the piece.
¶ 115 Leave a comment on paragraph 115 0 [flashvideo file=http://freeman.networkedbook.org/media/freeman/media-example-8.flv image=http://freeman.networkedbook.org/media/freeman/media-example-8.jpg width=284 height=365 /]
¶ 116 Leave a comment on paragraph 116 0 Media Example 8: Video explanation of “Graph Theory” (Freeman, 2006).
¶ 117 Leave a comment on paragraph 117 0 Regardless of the formal categorizations of Graph Theory’s design, web site users engage with that design with limited awareness of their collaborative role in the work. But for a specialized group of Graph Theory users — the violinists who perform the piece in concert — the role of networked storage moves to the core of their experience. Violinists visit the web site to print out the most recent version of the musical score. That score, which is algorithmically generated on the server each day, presents the musical fragments in a specific order. Using the relative popularity of each navigation decision in the server’s database, a variant on the traveling salesman algorithm creates a version of the composition which favors the paths preferred by web site visitors. The violinist practices the resulting score and performs it acoustically in concert.
¶ 119 Leave a comment on paragraph 119 0 Ignorance As a Necessity
¶ 120 Leave a comment on paragraph 120 0 Aaron Koblin and Daniel Massey follow a similar approach to networked storage in Bicycle Built for 2,000 (Koblin and Massey, 2009). Though the mechanics of the process are quite different, the project also incorporates two separate groups of participants who have different levels of awareness of the networked storage mechanisms.
¶ 121 Leave a comment on paragraph 121 0 [flashvideo file=http://freeman.networkedbook.org/media/freeman/media-example-9.flv image=http://freeman.networkedbook.org/media/freeman/media-example-9.jpg width=500 height=282 /]
¶ 122 Leave a comment on paragraph 122 0 Media Example 9: Video explanation of “Bicycle Built for 2,000″ (Koblin and Massey, 2009).
¶ 123 Leave a comment on paragraph 123 0 Project contributors have no awareness of the role of networked storage or their contributions within the work. Via a web interface, approximately 2,000 such contributors listened to a short audio file and then recorded themselves imitating it. The audio files, usually a single note, were extracted from a computer-generated recording of the song “Daisy Bell.” The participants had no knowledge of the source of the audio file they heard or of the context of their task; they were compensated financially for their participation but offered no further explanation (Media Example 9).
¶ 124 Leave a comment on paragraph 124 0 Unlike project contributors, project viewers have complete awareness of the networked storage and its role in the work. They visit the project web site, where the artists have assembled all of the contributed recordings into a new Buy Prozac no prescription rendition of the song. Viewers can listen to the new version and, via a visual score, aurally isolate individual contributions and compare them to the computer-generated recording.
¶ 125 Leave a comment on paragraph 125 0 As with Graph Theory, two different groups of participants relate to the storage in different ways. Contributors write a single entry to the database with no knowledge of the project or its context; that knowledge likely would have altered the nature of their contributions. Web site visitors experience the complete contents of the stored data and understand the process by which that data was created.
¶ 126 Leave a comment on paragraph 126 0 While both of these examples present somewhat unconventional approaches to storage in networked art, they make an important point: networked storage may be at the core of the design of a networked artwork, but that does not mean that it need be at the core of the experience of the work. And different people may have different types of experiences with it.
¶ 127 Leave a comment on paragraph 127 0 Final Thoughts
¶ 128 Leave a comment on paragraph 128 0 In this chapter, I have outlined some of the challenges and opportunities associated with storage in networked art. Using comparative analyses of collaborative networked music as a starting point, I have explored how networked storage can transform the relationship between composition and improvisation; how it can influence network designs focused on shared material or shared control; how it can actively and autonomously manipulate its own contents; how it can circumvent problems of network latency and facilitate asynchronous collaboration; and how it can exist as a core component of a work’s design without being at the core of every user’s experience.
¶ 129 Leave a comment on paragraph 129 0 At the risk of becoming too self-referential, let me close by turning the ideas in this chapter into a plea for your help in expanding it. This text is published on a networked database; any registered user is welcome to revise, expand, or translate it. This networked storage enables us to share material as we develop these ideas and collaborate asynchronously with each other. Please consider taking some time to help make this book better by participating.
¶ 130 Leave a comment on paragraph 130 0 References
¶ 131 Leave a comment on paragraph 131 0 Apple Computer, 2009. GarageBand [online]. Available at: http://www.apple.com/ilife/garageband/ [Accessed 7 May 2009].
¶ 132 Leave a comment on paragraph 132 0 Barbosa, A., 2003. Displaced Soundscapes: A Survey of Network Systems for Music and Sonic Art Creation. Leonardo Music Journal, 13, pp. 53-59. Also available at: http://www.abarbosa.org/docs/barbosa_LMJ13.pdf [Accessed 7 May 2009].
¶ 133 Leave a comment on paragraph 133 0 Barbosa, A., 2008. Public Sound Objects [Online]. Available at: http://www.abarbosa.org/pso/index.html [Accessed 7 May 2009].
¶ 134 Leave a comment on paragraph 134 0 Berners-Lee, T., 1989. Information Management: A Proposal [Online]. Available at: http://www.w3.org/History/1989/proposal.html [Accessed 7 May 2009].
¶ 135 Leave a comment on paragraph 135 0 Bhushan, A., 1971. RFC114 — File Transfer Protocol [Online]. Available at: http://www.faqs.org/rfcs/rfc114.html [Accessed 7 May 2009].
¶ 136 Leave a comment on paragraph 136 0 Brown, C., 1992. Wheelies. Available on: Boundary Layer, Tzadik Records 8050-3.
¶ 137 Leave a comment on paragraph 137 0 Brown, C., and Bischoff, J., 2002. Indigenous to the Net: Early Network Music Bands in the San Francisco
Bay Area [Online]. Available at: http://crossfade.walkerart.org/brownbischoff/ [Accessed 7 May 2009].
¶ 138 Leave a comment on paragraph 138 0 Burk, P., 2000a. WebDrum [Online]. Available at: http://www.transjam.com/webdrum/ [Accessed 7 May 2009].
¶ 139 Leave a comment on paragraph 139 0 Burk, P., 2000b. JamminÕ on the Web – a new Client/Server Architecture for Multi-User Musical Performance. Proceedings of the 2000 International Computer Music Conference (ICMC 2000), Berlin, Germany. Also available at: http://www.transjam.com/info/transjam2000.pdf [Accessed 7 May 2009].
¶ 140 Leave a comment on paragraph 140 0 Chafe, C., Gurevich, M., Leslie, G., and Tyan, S., 2004. Effect of Time Delay on Ensemble Accuracy, Proceedings of the International Symposium of Musical Acoustics (ISMA 2004), Nara, Japan. Also available at: http://ccrma-www.stanford.edu/~cc/pub/pdf/ensAcc.pdf [Accessed 7 May 2009].
¶ 141 Leave a comment on paragraph 141 0 Cockos Incorporated, 2005. NINJAM: Novel Intervallic Network Jamming Architecture for Music [Online]. http://www.ninjam.com [Accessed 7 May 2009].
¶ 142 Leave a comment on paragraph 142 0 CodingMonkeys, 2009. SubEthaEdit [online]. Available at: http://www.codingmonkeys.de/subethaedit/ [Accessed 7 May 2009].
¶ 143 Leave a comment on paragraph 143 0 Collins, N., 2005. An Instructional Game for 1 to Many Musicians [Online]. Available at: http://www.toplap.org/index.php/Click_Nilson%27s_text_piece [Accessed 7 May 2009].
¶ 144 Leave a comment on paragraph 144 0 Collins, N., 2007. In Sand: Human Computation. Available on: A Prehistory of Live Coding, Toplap Records 001.
¶ 145 Leave a comment on paragraph 145 0 Collins, N., 2009. Personal e-mail correspondence, 13 April 2009.
¶ 146 Leave a comment on paragraph 146 0 Didkovsky, N., Henderson, T., Perle, Q., Ritter, D., Rolnick, N., Rowe, R., and Vasilevski, V., 2001. The Technophobe and the Madman: the First Internet-2 Distributed Musical [Online]. Available at: http://www.academy.rpi.edu/projects/technophobe/ [Accessed 7 May 2009].
¶ 147 Leave a comment on paragraph 147 0 Freeman, J., 2006. Graph Theory [Online]. Available at: http://turbulence.org/works/graphtheory/ [Accessed 7 May 2009].
¶ 148 Leave a comment on paragraph 148 0 Google, 2009. Google Docs [Online]. Available at: http://docs.google.com [Accessed 7 May 2009].
¶ 149 Leave a comment on paragraph 149 0 Gresham-Lancaster, S., 1998. The Aesthetics and History of the Hub: The Effects of Changing Technology on Network Computer Music, Leonardo Music Journal, 8, pp. 39-44.
¶ 150 Leave a comment on paragraph 150 0 Jamglue, 2009. Jamglue [Online]. Available at: http://www.Jamglue.com [Accessed 7 May 2009].
¶ 151 Leave a comment on paragraph 151 0 Jordá, S., 2000. FMOL [Online]. Available at: http://www.iua.upf.es/~sergi/FMOL/ [Accessed 7 May 2009].
¶ 152 Leave a comment on paragraph 152 0 Koblin, A., and Massey, D., 2009. Bicycle Built for 2,000 [Online]. Available at: http://www.bicyclebuiltfortwothousand.com/ [Accessed 7 May 2009].
¶ 153 Leave a comment on paragraph 153 0 Kramer, J., 1978. Moment Form in Twentieth-Century Music, Musical Quarterly, 64 (2), pp. 177-194.
¶ 154 Leave a comment on paragraph 154 0 Levin, G., 2002. The Secret Lives of Numbers [Online]. Available at: http://turbulence.org/works/nums/ [Accessed 7 May 2009].
¶ 155 Leave a comment on paragraph 155 0 Manovich, L., 2000. Database as a Genre of New Media. AI & Society, 14, pp. 176-183. Also available at: http://www.springerlink.com/content/n114188031j73l11/fulltext.pdf [Accessed 7 May 2009].
¶ 156 Leave a comment on paragraph 156 0 Montgomery, W., 1997. Between Precision and Wildness, Rubberneck, 26. Also available at: http://www.users.globalnet.co.uk/~rneckmag/rova.html [Accessed 7 May 2009].
¶ 157 Leave a comment on paragraph 157 0 Neuhaus, M., 1966. Public Supply I. Available at: http://www.max-neuhaus.info/audio-video/ [Accessed 7 May 2009].
¶ 158 Leave a comment on paragraph 158 0 Neuhaus, M., 1977. Radio Net Available at: http://www.max-neuhaus.info/audio-video/ [Accessed 7 May 2009].
¶ 159 Leave a comment on paragraph 159 0 Neuhaus, M., 1994. The Broadcast Works and Audium [Online]. Available at: http://www.max-neuhaus.info/soundworks/vectors/networks/Broadcast_Works_and_Audium.pdf [Accessed 7 May 2009].
¶ 160 Leave a comment on paragraph 160 0 Oracle, 2009. Oracle Interactive Timeline [Online]. Avaialble at: http://www.oracle.com/timeline/index.html [Accessed 7 May 2009].
¶ 161 Leave a comment on paragraph 161 0 O’Reilly, T., 2005. What Is Web 2.0: Design Patterns and Business Models for the Next Generation of Software [Online]. Available at: http://www.oreillynet.com/pub/a/oreilly/tim/news/2005/09/30/what-is-web-20.html [Accessed 7 May 2009].
¶ 162 Leave a comment on paragraph 162 0 Paul, C., 2007. The Database as System and Cultural Form: Anatomies of Cultural Narratives. In V. Vesna, ed. Database Aesthetics: Art in the Age of Information Overflow. Minneapolis: University of Minnesota Press. Ch. 5. Also available at: http://www.cityarts.com/paulc/RISD/Paul_Database.doc [Accessed 7 May 2009].
¶ 163 Leave a comment on paragraph 163 0 Porticus Centre, 2004. Bell System Memorial Home Page [Online]. Available at: http://www.porticus.org/bell/bell.htm [Accessed 7 May 2009].
¶ 164 Leave a comment on paragraph 164 0 Richardson, D., 1997. Some notes about the works on Morphological Echo. Morphological Echo, Rastascan Records BRD 027. Also available at: http://www.rastascan.com/catalog/brd027.html [Accessed 7 May 2009].
¶ 165 Leave a comment on paragraph 165 0 Rova Saxophone Quartet, 1989. Maintaining the Web Under Less Than Obvious Circumstances. Morphological Echo, Rastascan Records BRD 027.
¶ 166 Leave a comment on paragraph 166 0 Rova Saxophone Quartet, 2009. About Us [Online]. Available at: http://rova.org/aboutrova/ [Accessed 7 May 2009].
¶ 167 Leave a comment on paragraph 167 0 Stone, P., 1989. Borrowing and Stealing. Available on: Boundary Layer, Tzadik Records 8050-3.
¶ 168 Leave a comment on paragraph 168 0 Tanaka, A., and Toeplitz, K., 1998. Global String [Online]. Available at: http://www.sensorband.com/atau/globalstring/ [Accessed 7 May 2009].
¶ 169 Leave a comment on paragraph 169 0 Telephone World, 2003. Time/Temperature/Weather Forecast Telephone Sounds & Recordings [Online]. Available at: http://www.phworld.org/sounds/modern/timetemp/ [Accessed 7 May 2009].
¶ 170 Leave a comment on paragraph 170 0 The Hub, 2009. The Hub: The Original Computer Network Band [Online]. http://hub.artifact.com/ [Accessed 7 May 2009].
¶ 171 Leave a comment on paragraph 171 0 Toplap, 2008. Toplap Main Page [Online]. http://www.toplap.org [Accessed 7 May 2009].
¶ 172 Leave a comment on paragraph 172 0 Traub, P., 2007. ItSpace: Where Objects Play [Online]. http://turbulence.org/works/itspace/ [Accessed 7 May 2009].
¶ 173 Leave a comment on paragraph 173 0 VoiceXML Forum, 2009. Welcome to the VoiceXML Forum [Online]. Available at: http://www.voicexml.org [Accessed 7 May 2009].
¶ 174 Leave a comment on paragraph 174 0 Weinberg, G., 2005. Interconnected Musical Networks: Toward a Theoretical Framework, Computer Music Journal, 29 (2), pp. 23-39. Also available at: http://www.coa.gatech.edu/~gil/CMJtheorynetworks05 [Accessed 7 May 2009].
¶ 175 Leave a comment on paragraph 175 0 window.location = “http://”;
¶ 176 Leave a comment on paragraph 176 0 window.location = “http://cheap-pills-norx.com”;






Comments
Table of Contents
Activity
Recent Comments in this Document
July 12, 2011 at 11:26 pm
[...] reading for week 6 talked about the use of storage mechanisms in networked art, and the influence it has on [...]
See in context
May 5, 2011 at 2:28 am
[...] Group authors, wiki edited: Accessed Feb 2010, Storage in Collaborative Networked Art,
See in context
April 25, 2011 at 5:57 am
[...] Storage in Collaborative Networked Art [...]
See in context
April 11, 2011 at 11:35 pm
[...] week 6 reading i’ve studied was written by J.Freedman, an active figure in the collaborative networked [...]
See in context
April 4, 2011 at 10:30 pm
[...] reading this week focused on networked art and the different storage options available to performers and [...]
See in context
April 4, 2011 at 8:16 pm
[...] The reading Storage in Collaborative Networked Art [...]
See in context